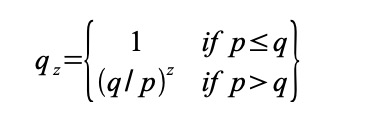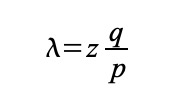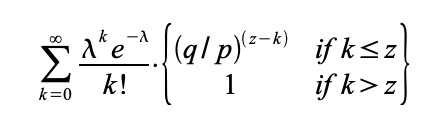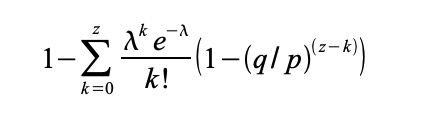注:初步翻译;仅作收录。
Note: Preliminary translation; accepted only.
Satoshi Nakamoto
satoshin@gmx.com
www.bitcoin.org
一个纯粹的点对点电子现金版本,将允许在线支付,直接从一方发送到另一方,无需通过金融机构。
A purely point-to-point electronic cash version would allow online payments to be sent directly from one party to the other without having to pass through a financial institution.
数字签名提供部分解决方案,但是,如果仍然需要受信第三方来防止双重花费,此类解决方案的主要优势则失去。
Digital signatures provide part of the solution, but the main advantage of such a solution is lost if a trusted third party is still needed to prevent double costs.
我们提出双重花费问题的一个解决方案:使用一个点对点网络。通过将交易哈希到不断进行的基于哈希的 proof-of-work 链中,网络对交易打上时间戳,从而形成一个记录,如果不重做该 proof-of-work,这个记录便无法被更改。最长链,不仅可作为所被见证的事件序列的证明,还可证明它来自最大的 CPU 算力集合。只要大多数 CPU 算力由不合作攻击网络的节点控制,这些算力就将生成最长链,并超过攻击者。网络本身需要最小结构。消息被尽力传播,节点可随意离开,也可随意重新加入网络,接受最长 proof-of-work 链,作为这些节点离开时所曾发生事件的证明。
We propose a solution to the problem of double spending: a network of point-to-points. By putting the transaction into an ongoing Hashi-based proof-of-work chain, the network puts a time stamp on the transaction, thus creating a record that cannot be changed without redrawing the proof-of-work. The longest chain, not only as proof of the sequence of events witnessed, can prove that it comes from the largest CPU collection of computing power. As long as most CPUs are controlled by nodes of uncooperative attacks on the network, they generate the longest chain and exceed the attackers.
互联网上的商业,几乎完全依赖金融机构作为受信第三方,来处理电子支付。虽然对于大多数交易而言,此系统运行得足够好,但其仍然遭受基于信任的模型的固有缺陷。完全不可逆转的交易,实际上是不可能的,因为金融机构无法避免调解纠纷。调解成本提高了交易成本,这些交易成本的上升,限制了最小额实际交易规模( minimum practical transaction size ),切断了小额非正式交易( small casual transactions )的可能性;还有更大成本——丧失为不可逆服务进行不可逆支付的能力 ( there is a broader cost in the loss of ability to make non-reversible payments for nonreversible services )。因为有逆转的可能,对信任的需求在扩大。商家必须对他们的客户保持警惕,为了所需之外的更多信息,他们不断烦扰客户。一定比例的欺诈被认为不可避免。这些成本和应付款项( payment )的不确定性,可通过亲身使用实物货币来避免,但是,不存在这样的机制——在无可信方的情况,使应付款项跨越通信渠道 ( no mechanism exists to make payments over a communications channel without a trusted party )。
Business on the Internet relies almost entirely on financial institutions to handle electronic payments as trusted third parties. While the system works well enough for most transactions, it still suffers from inherent flaws in a trust-based model. Complete irreversible transactions are practically impossible, because financial institutions cannot avoid mediating disputes. The costs of mediation raise transaction costs, which limit the size of the smallest actual transactions (minimum commercial transactions size), cut off the possibility of small informal transactions (small commercial transactions). There are larger costs - the loss of the ability to make unreversible payments for irreversible services (there is a widespread cost in the loss of the loss of the goods of un-reversible services).
所需要的是,基于加密证明,而非基于信任的电子支付系统,允许任何有意愿的两方,直接相互交易,而无需可信第三方。在计算上无法逆转的交易,将保护卖家免受欺诈;常规的托管机制( routine escrow mechanisms ),可以很容易地实现,以保护买家。
What is needed is an electronic payment system based on encryption, rather than trust, that allows any willing party to deal directly with each other without the need for a credible third party. Arithmetical irreversible transactions will protect sellers from fraud; conventional trusteeship mechanisms (routine escrow mechanisms) can be easily achieved to protect buyers.
在本文,我们提出一个方案,解决双重花费问题——即,使用一个点对点分布式时间戳服务器,生成交易时间顺序的计算证明。只要诚实节点所共同控制的 CPU 算力 ,比攻击者节点合作组所共同控制的更多,该系统就是安全的。
In this paper, we propose a solution to the problem of double costs -- i.e., using a point-to-point time stamp server to generate a calculation of the chronology of transactions. The system is safe as long as the CPUs that are controlled jointly by honest nodes are more powerful than those jointly controlled by the attacking node group.
我们将一枚电子币 ( an electronic coin ) 定义为一条数字签名链( We define an electronic coin as a chain of digital signatures )。每个拥有者,通过对 previous transaction 及下一个拥有者公钥的哈希进行数字签名,并将这些签名添加到该币末尾,从而将该币传输到下一个拥有者。收款人(payee)可以验证该签名,以验证该所有权链。
We define an electronic coin as a digital coin as a chain of digital signatures. Each owner, by digitally signing the previious translation and the next owner's public key, adds the signature to the end of the currency, thereby transmitting the currency to the next owner. The payee (payee) can verify the signature to verify the chain of title.
问题是,收款人无法验证其中一个拥有者没有双重花费过该币。一种常见解决方案是,引入一个受信中央机构或造币厂( mint ),由它检查每笔交易是否双重花费。在每次交易后,币必须退回造币厂,然后,发行一枚新币,且只有直接从造币厂发行的币,才被可信没有被双重花费。这个解决方案的问题是,整个货币系统的命运,依赖于运营造币厂的公司,每笔交易都必须通过造币厂,就像银行一样。
The problem is that the payee is unable to verify that one of the owners did not spend the currency twice. A common solution is to introduce a trusted central agency or a money-making company, which will check whether each transaction costs twice. After each transaction, the currency must be returned to the currency-making plant, and then issued a new currency, and only the currency issued directly from the money-making plant will be credible and not cost twice.
我们需要一种方法,来让收款人知道,之前的拥有者,没有签署过任何更早交易。出于我们的目的,最早的交易才是计入的交易,所以,我们不关心其后的双重花费尝试。确认一个交易不存在的唯一方法是,知道所有交易。在基于造币厂的模型中,造币厂知道所有交易,并裁决哪笔交易首先到达。为了在没有可信方的情况下,实现这一目标,交易必须被公开声明[1],并且,我们需要一个系统,让参与者就“交易被接收顺序的单一历史( a single history of the order in which they were received ) ”达成共识。收款人需要这个“证明”——在每次交易时,大多数节点都达成共识,这笔交易是第一次被接收到。
We need a way for the payee to know that the previous owner did not sign any earlier transactions. For our purposes, the earliest transaction is the transaction in which it is counted, so we do not care about the subsequent double expense attempt. The only way to confirm that a transaction does not exist is to know all the transactions. In a model based on currency mills, the money mill knows all the transactions and decides which transactions arrives first. In order to achieve this, the transaction must be publicly declared [1] , and we need a system for participants to reach a consensus on "a single history of the order of transactions in which they were received".
我们提出的解决方案,开始于时间戳服务器。时间戳服务器的工作原理是,将 items 的区块的哈希进行时间戳( taking a hash of a block of items to be timestamped ),并广泛发布该哈希,如在 newspaper 或 Usenet post 中那样?[2-5]?。显然,为进入哈希,时间戳用以证明在当时数据必然已经存在。每个时间戳包含其哈希中的之前时间戳,形成一条链,通过每个附加时间戳加强其之前的所有时间戳。
The solution we're proposing is starting with the time-stamping server. The working principle of the time-tamping server is to take a cash of a block of items to be timestamped and to publish it widely, as in the newspaper or Usset post? . Obviously, for the purpose of entering Hash, the time-stamp is used to prove that the data must have existed at that time. Each time-stamp contains its time-stamp, forming a chain that strengthens all its time-stamps by each additional time-stamp.
要实现点对点分布式时间戳服务器,我们将需要使用 Proof-of-Work 系统,类似 Adam Back 的 Hashcash [6],而不是 newspaper 或 Usenet posts。Proof-of-Work,涉及扫描一个值,当这个值被哈希时,例如通过 SHA-256,该哈希开始于很多 0 bits (a number of zero bits)。所需平均工作量是所需 0 bits 数量的指数,并且可以通过执行单个哈希来进行验证。
To achieve a point-to-point timetamp server, we will need to use Proof-of-Work systems similar to Adam Back's Hashcash [6], rather than newspaper or Usenet pots. Proof-of-Work, involves scanning a value that starts with a lot of 0 bits (a number of zero bits) when it comes to Hashi, for example, through SHA-256. The average workload is an index of 0 bits required and can be verified by executing individual Hash.
对于我们的时间戳网络,我们执行 Proof-of-Work,是通过递增区块中的随机数,直到一个特定值被找出,将所需 0 bits 给该区块哈希 。一旦所花费 CPU 工作量,满足 Proof-of-Work,该区块就无法被更改,除非重做该工作。之后区块,链于其后,更改该区块所需工作,将包括重做其之后的所有区块。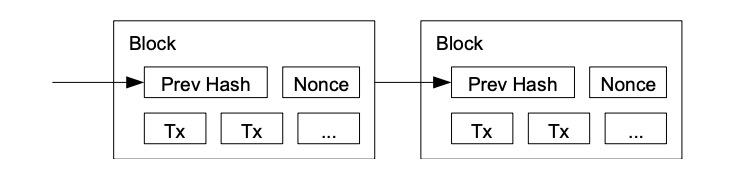
For our time stamping network, we execute Proof-of-Work, which is a random number in an incremental block, until a specific value is identified, with the required 0 bits given to Hashi. Once the CPU workload is spent, the block cannot be changed unless it is redoneed.
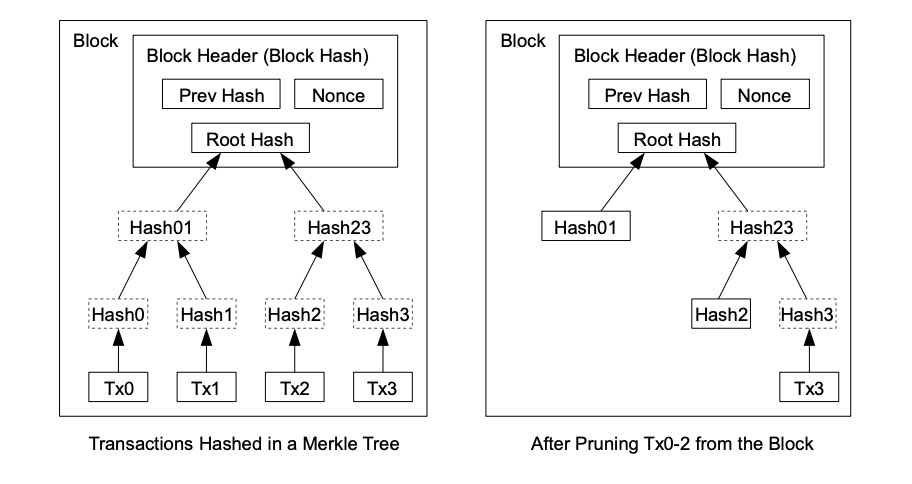
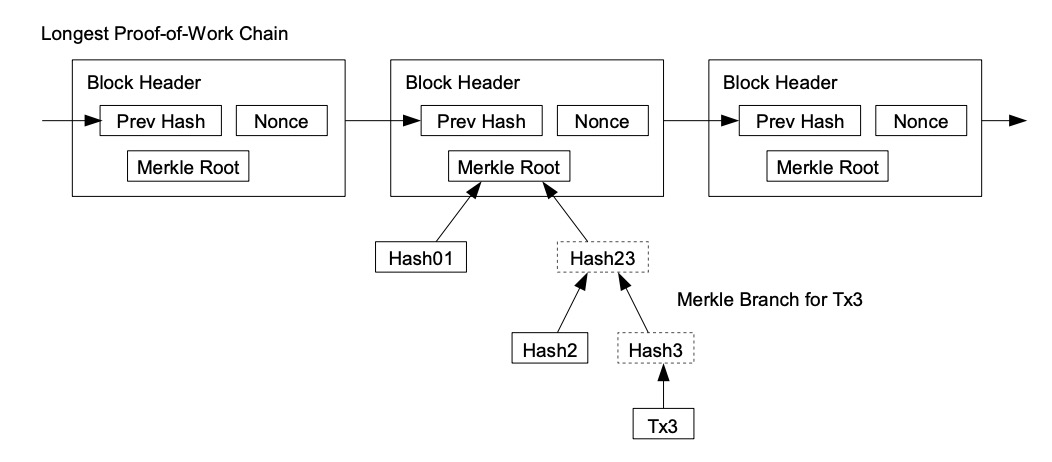
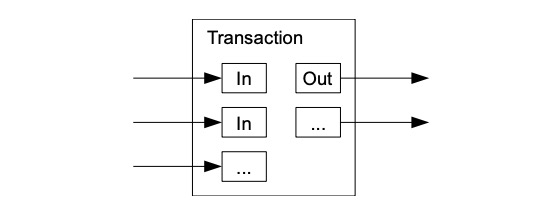
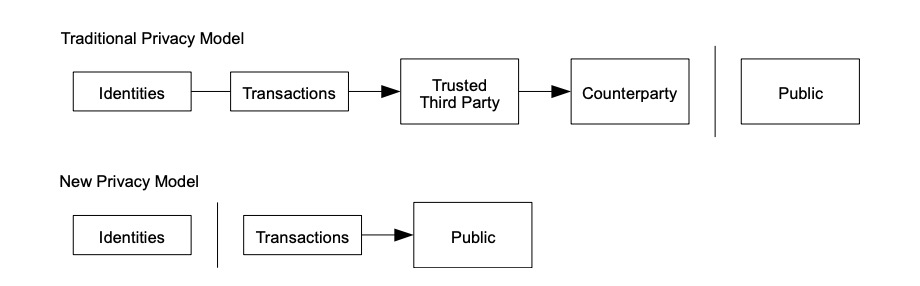
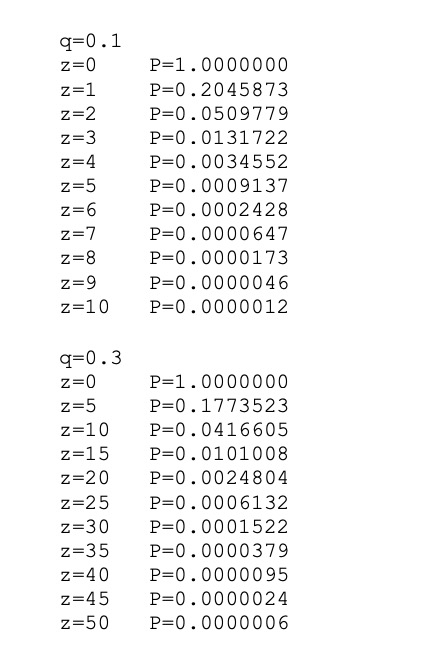
Proof-of-Work 还解决在大数决策中确定代表( determining representation ) 的问题。如果大数( the majority )是基于一 IP 地址一票,可能会被任何能够分配许多 IP 的人所破坏。本质上,Proof-of-work 是一 CPU 一票。大数决策由最长链表示,最长链拥有投入其中的最大 proof-of-work effort 。如果大部分 CPU 算力由诚实节点控制,诚实链将增长最快并超过任何竞争链。如果要修改某个过去的区块,攻击者必须重做该区块及其之后的所有区块的 proof-of-work ,然后追赶并超越诚实节点的 work 。我们将稍后说明,随着后续区块的添加,速度慢的攻击者( a slower attacker )赶上的概率,呈指数级递减。 Proof-of-Work also solves the problem of determining representation in a large number of decisions. If the large number of votes is based on an IP address, it may be destroyed by anyone who can distribute many IPs. Essentially, Proof-of-work is a CPU. Large-numbered decisions are expressed by the longest chain, with the largest proof-of-work effort available. If most CPUs are controlled by honest nodes, the chain of honesty will grow fastest and exceed any competitive chain. If a previous block is to be modified, the attacker will have to redo the proof-of-work of the block and all the blocks that follow it, and then catch up and go beyond the honest section of the work. We will explain later the probability of a slow attacker (a slower attacker) catching up as the next block is added. 为了弥补随着时间推移,硬件速度的提高及运行节点所带来的利益的变化,proof-of-work 难度由 a moving average targeting an average number of blocks per hour 确定。如果区块生成得太快,难度会提升。 In order to compensate for the change in hardware speed over time and the benefits of running nodes, the difficulty is determined by a moving array number of blocks per hour. If blocks are generated too quickly, the difficulty increases. 网络运行步骤如下: The network operates in the following steps: 节点们始终将最长链视为正确链,并将继续致力于扩展它。如果同时,两个节点广播下一个区块的不同版本,则一些节点可能先接收到一个或另一个版本。在这种情况下,他们致力于他们所接收到的第一个,但保存另一个分支,以防这另一个分支变得更长。当下一个 proof of-work 被找到,并且一个分支变得更长时,这种关系将被打破;然后,致力于另一个分支的节点,将转向更长的那个分支。 Nodes always view the longest chain as the right one, and will continue to work to expand it. If, at the same time, two nodes broadcast different versions of the next block, some nodes may receive one or another version first. In this case, they commit themselves to the first one they receive, but keep another branch in case the other branch becomes longer. When the next proof of work is found and one branch becomes longer, the relationship will be broken; then, the node of another branch will be turned to the longer branch. 新的交易广播不必然需要到达所有节点。只要它们到达许多节点,它们将会很快( before long )进入一个区块。区块广播也容忍消息丢失。如果一个节点没有收到一个区块,在接收到下一个区块,并意识到它丢失了一个区块时,它将会提出请求。 New trade broadcasts do not necessarily have to reach all nodes. As long as they reach many nodes, they will soon enter a block. Block broadcasts also tolerate the loss of news. 按照惯例,区块中的第一笔交易,是一笔特殊交易,这笔交易启动了一枚新币,由该区块的创建者所拥有。这增加了对节点的一个激励,激励节点支持网络,并提供一种方式,来将币初始分发到流通中,因为没有中央权威机构来发行币。稳定增加的新币数量,就像淘金者消耗资源而增加的流通中的黄金。在我们的例子中,消耗的是 CPU 时间和电能( CPU time and electricity )。 As is customary, the first transaction in a block is a special transaction, which triggers a new currency, owned by the founders of the block. This adds an incentive to the node, stimulates the node support network, and provides a way to distribute the currency initially to circulation, since there is no central authority to issue the currency. The number of new currency increases steadily, like the amount of gold in circulation that the gold hunter consumes resources. In our case, the CPU time and electricity is consumed. 激励节点支持网络,还可以通过交易费用来资助。如果一个交易的输出值小于它的输入值,差额就是一个交易费,交易费被添加到包含该交易的区块的激励值中( that is added to the incentive value of the block containing the transaction )。一旦预定数量的币已进入流通,激励机制就可以完全过渡给交易费用,完全无通胀。 Incentive node supports the network, which can also be financed by transaction costs. If the value of a transaction is less than its input value, the difference is a transaction fee, which is added to the incentive value of the block containing the transaction. Once the intended amount of currency is in circulation, the incentive mechanism can be fully transferred to the transaction cost, completely free of inflation. 激励机制可能有助于鼓励节点保持诚实。如果一个贪婪的攻击者,能够比所有诚实节点组装更多 CPU 算力,他必须做出选择,是用这些算力来偷回自己支付出的款项,欺骗别人,还是用来产生新币。他应该发现,相比破坏系统以及破坏自己财富的有效性,遵守规则更有利可图,因为这些规则有利于他获得的新币,比其他人加起来还要多。 Incentives can help encourage nodes to remain honest. If a greedy attacker can assemble more CPU than all honest nodes, he must choose whether to use them to steal money from himself, deceive others, or use them to generate a new currency. He should find it more profitable to comply with rules than to destroy the system and the effectiveness of his own wealth, because these rules favour his acquisition of a new currency, more than others add up. 一旦一枚币中的最新交易被沉于足够多的区块之下( Once the latest transaction in a coin is buried under enough blocks ),它之前的已花费交易就可以丢弃掉,以节省磁盘空间。为了在不破坏区块哈希的情况下,促进( facilitate )这一点,在 Merkle Tree [7] [2] [5]中对交易进行哈希,只有 root 包含在区块哈希中。然后可以通过截断 branches of the tree ( stubbing off branches of the tree )来压缩旧区块。不需要存储内部哈希( interior hashes )。 Once the latest transaction in a currency is buried under enough blocks, it can be discarded in order to save disk space by spending on previous transactions. To promote this without destroying the block, in Merkle Tre < span style="color: #800000;" >[7][2] the deal is contained in the block. The old block can then be compressed by cutting the branches of the block off branches of the block. 不包含交易的一个区块头( A block header with no transactions )大约是 80 bytes。如果我们假设每 10 分钟生成一个区块,则 80 bytes* 6 * 24 * 365=4.2MB / 年。在 2008 年,计算机系统的 RAM 通常为 2GB,而摩尔定律预测当前增长率为 1.2GB/年 ,因此存储应该不是问题,即使区块头必须保存在内存 ( memory ) 中。 A block header with no transactions is about 80 bytes. If we assume that a block is generated every 10 minutes, 80 bytes* 6 * 24 * 365 = 4.2MB/ year. In 2008, the computer system RAM is usually 2GB, while Moore's Law predicts the current growth rate of 1.2 GB/ year, storage should not be a problem, even if the block head must be kept in the memory (mory). 无需运行全网络节点即可验证支付,这是可能的。用户只需保留最长 proof-of-work 链的区块头的副本,他可以通过 querying 网络节点,直到他确信他拥有最长链,并获得 Merkle 分支(? 该 Merkle 分支将交易链接到其时间戳所处区块 ),就能获得这个副本。他不能为自己核查交易,但是通过将这笔交易链接到链中的某个地方,他可以看到一个网络节点已接受这笔交易,并且在进一步确认网络已接受它之后,区块被添加( blocks added )。 It is possible to verify payment without running a full network node. The user simply needs to keep a copy of the block head of the maximum proof-of-work chain, and he can use the querying network node until he is convinced that he has the longest chain and has access to the Merkle branch (the Merkle branch that links the transaction to its time-stamped block). He cannot verify the transaction for himself, but by linking the transaction to a place in the chain, he can see that a network node has accepted the transaction and that the block has been added (blocks added) after further confirmation that the network has accepted it. 因此,只要诚实节点控制网络,验证就是可靠的,但如果网络被攻击者制服,则验证更容易遭受攻击( more vulnerable )。虽然网络节点可以为自己验证交易,但只要攻击者能够继续制服网络,简化方式就会被攻击者的伪造交易( fabricated transactions )所欺骗。防范这种情况的一种策略是,当网络节点检测到一个无效区块时,接收来自这些网络节点的警报,提示(prompting )用户软件下载完整区块及被警告的交易, 以确认该不一致。接收经常性支付款项的企业,将可能仍然希望运行自己的节点,以获得更独立的安全性和更快的验证。 As a result, authentication is reliable as long as honest nodes control the network, but verification is more likely if the network is under the uniform of the attacker. While the network nodes can validate the transaction for themselves, simplification will be deceived by the attacker’s forged transactions as long as the network can continue to dominate the network. One strategy to prevent this is to receive alerts from these network nodes when they detect an invalid block, and to point out that the user software downloads the entire section and the transactions that have been warned in order to confirm the inconsistency. Businesses that receive regular payments may still want to run their own nodes to obtain more independent security and faster verification. 虽然单独处理币( handle coins individually )是可能的,但是,对转账中的每一分钱产生一笔单独交易,这很不便利。为了允许价值的拆分和组合,交易包含多个输入和输出( transactions contain multiple inputs and outputs )。通常,将会有一单个输入(来自一个较大的上一个交易 from a larger previous transaction )或多个输入( 组合了多个较小金额);以及最多两个输出:一个用于支付,一个将零钱(如果有)返回给发送者。 While it is possible to deal alone with currencies (handle coins individually), it is not easy to generate a single transaction for each fraction of the money transferred. To allow splits and combinations of value, the transaction contains multiple inputs and outputs (transactions contain multipots and outputs). Normally, there will be a single input (from a larger previous transaction) or multiple inputs (a combination of smaller amounts); and a maximum of two outputs: one to pay for and one to return petty money (if any) to the sender. 需要注意的是 fan-out ( 在其中,一笔交易依赖于多笔交易,而这多笔交易依赖于更多交易 where a transaction depends on several transactions, and those transactions depend on many more ),在这里不是问题。不再需要提取交易历史的完整独立副本( There is never the need to extract a complete standalone copy of a transaction's history )。 There is never the need to extract a complete stand-alone copy of a transaction's history. 传统的银行模式,通过对相关方和可信第三方的信息访问行为进行限制,来实现一定程度的隐私。公开宣布所有交易——其必要性,排除了这种传统方法,但仍可通过打破另一处的信息流,来维护隐私:通过保持公钥匿名。公众可以看到某人正在向其他某人发送一笔金额,但是没有“与此交易有所链接的任何人”的相关信息( without information linking the transaction to anyone )。这类似证券交易所( stock exchanges )发布的信息水平,在证券交易所,个人交易的时间和规模 ( 即 “ tape ” ) 是公开的,但不泄露交易双方是谁。 The traditional banking model achieves a degree of privacy by restricting access to information by interested parties and credible third parties. Public disclosure of all transactions — the necessity of which precludes such traditional methods — can preserve privacy by breaking another flow of information: by keeping the public key anonymous. The public can see that a person is sending a sum of money to someone else, but there is no information about “anyone connected to this transaction” (outfomation of the transaction to anyone). This is similar to the level of information published by stock exchanges (stock exchanges), where the time and size of the individual transaction (i. e. g. “tape”) is public, but does not reveal who the parties are. 作为一个附加防火墙,应为每笔交易使用一个新密钥对( a new key pair ),以防止此交易与一个普通所有者相链接。对于多输入交易( multi-input transactions ),某些链接仍不可避免,多输入交易必然泄露其多输入属于同一拥有者。风险在于,如果一个密钥的拥有者被泄露,此链接可以揭示属于同一拥有者的其他交易。 As an additional firewall, a new key pair should be used for each transaction to prevent the transaction from being linked to an ordinary owner. For multiple-input transactions, some links are still inevitable, and multiple-input transactions necessarily reveal that they belong to the same owner. The risk is that if the owner of a key is disclosed, the link reveals other transactions belonging to the same owner. 我们考虑一下这种场景,一个攻击者,试图比诚实链更快地生成一个替代链( alternate chain )。即使这已经完成,它也不会使系统对任意更改(如凭空创造价值,或拿走从来不属于攻击者的钱)开放通道。节点将不会认可一笔无效交易作为支付款项( Nodes are not going to accept an invalid transaction as payment ),诚实节点将永不会接受包含这些无效交易的区块。一个攻击者只能尝试更改他自己交易中的一笔,以拿回他最近花掉的钱( An attacker can only try to change one of his own transactions to take back money he recently spent )。 We consider this scenario, where an attacker tries to produce an alternative chain faster than an honest chain. Even if this is done, it will not allow the system to open access to arbitrary changes (e.g. to create value in vain or to take money that never belonged to the attacker). Nodes are not going to accept an invalid transaction as a payment, and honest nodes will never accept blocks containing these invalid transactions. An attacker can only try to change one of his own transactions to take back money he recently spent. 诚实链和一个攻击者链之间的竞赛,可表征为一种二项式随机游走(Binomial Random Walk)。成功事件是,诚实链被一个区块所延展,其领先优势增加 +1 ;失败事件是,攻击者链被一个区块所延展,将差距缩小 -1 ( reducing the gap by -1 )。 The contest between the honesty chain and a chain of attackers can be characterized as a two-pronged random walk (Binomial Random Walk). The successful event is that the honesty chain is extended by a block, with its leading edge increased by +1; the failed event is that the chain of attackers is extended by a block, reducing the gap -1 (reducing the gap by -1). 攻击者在处于给定“亏损”状况( a given deficit )下,赶超诚实链的可能性,类似赌徒的破产问题。假设一个拥有无限信用的赌徒,开始于亏损状况 ( deficit ),然后,可能会进行无数次尝试,以试图达到盈亏平衡。我们可以计算他达到盈亏平衡的概率,或者一个攻击者追赶上诚实链的概率,如下 [8] : Assuming that a gambler with unlimited credit starts with a loss condition, then it may be tried countless times to try to achieve a profit/loss balance. We can calculate the probability that he will achieve a profit balance or that an attacker will catch an honest chain, as follows: [8] : 考虑到我们的假设 p > q,随着攻击者必须跟上的区块的数量的增加,攻击者追赶上诚实链的概率呈指数级下降。在处于不利的情况下,如果他没有在一开始就幸运地向前冲,当他落在后面,他追赶上的概率 ( chances ) 就会变得微乎其微。 Given our hypothesis p & gt; q, as the number of blocks the attackers have to keep up with, the likelihood of the attackers catching up with the honesty chain has declined exponentially. In a disadvantageous situation, if he has not been lucky enough to go forward in the first place, when he lags behind, his probability of catching up will become minimal. 我们现在考虑,一笔新交易的接收方,需要等待多长时间,才能充分确定发送方无法更改该笔交易。我们假设:该发送者是一个攻击者,他想让接收方相信,他付给接收方钱一段时间了;然后,发送方在一段时间后将钱支付返给自己。当这种情况发生,接收方将会收到警报,但发送方希望警报为时已晚。 We now consider how long it will take for the recipient of a new transaction to be fully certain that the sender will not be able to change the transaction. Let us assume that the sender is an attacker who wants to convince the recipient that he has been paying the recipient money for some time; then, the sender will return the money to himself after some time. When this happens, the receiving party will receive the alarm, but the sender hopes that it will be too late. 接收方生成一个新密钥对,在发送方签署交易前不久,将公钥提供给发送方。这可以防止发送方提前准备区块的链( a chain of blocks ),提前准备的方法是不断地 working on it ,直到他足够幸运地超前 get ,然后在那一刻执行该交易( This prevents the sender from preparing a chain of blocks ahead of time by working on it continuously until he is lucky enough to get far enough ahead, then executing the transaction at that moment )。一旦交易被发送,该不诚实发送方就开始秘密地 working on 包含他的交易的另一个版本的并行链( a parallel chain containing an alternate version of his transaction )。 The receiver generates a new key pair, which is given to the sender shortly before it signs the transaction. This prevents the sender from preparing the chain of blocks (a chain enough to get far enough ahead, then preparing the transaction at that moment). Once the transaction is sent, the dishonest sender starts to work on another version of his transaction (a parallel chain containing his transaction). 接收方等待,直到交易被添加到一个区块,z 个区块链接于它之后。接收方不知道攻击者所取得的确切进度,但如果假设诚实区块花费平均预期时间/区块( the honest blocks took the average expected time per block ),攻击者的潜在进展,将是具有预期值的泊松分布( a Poisson distribution with expected value ): The recipient waits until the transaction is added to a block, after which z blocks are linked. The recipient does not know the exact progress made by the attacker, but if the honest blocks take the average expected time/block (the honest block took the expected time per block), the potential progress of the attacker will be a Poisson distribution with expected value: 为了获得攻击者现在仍然能够追赶上的概率,我们将他所已经取得的每个进度额的泊松密度( the Poisson density for each amount of progress he could have made ), 乘以他从那时起能够追赶上的概率: In order to obtain the probability that the assailant will still be able to catch up, we multiply the density of every amount of progress he has achieved by the probability that he will be able to catch up from then on: 重新排列,以避免求和分布的无限尾( to avoid summing the infinite tail of the distribution ).. Rearranging to avoid subsuming the unlimited tail of the distribution.. 转换为 C code.... Convert to C code.... 运行一些结果,我们可以看到概率随 z 值的增加,呈指数下降。 当 P 小于 0.1%,求解 ... When P is less than 0.1%, solve... 我们提出了一种不依赖于信任的电子交易系统。我们开始于通常的数字签名币框架( framework of coins made from digital signatures ),这种框架提供了强有力的所有权控制( strong control of ownership ),但如果没有防止双重花费的方法,这种解决方案是不完全的。 We propose an electronic trading system that does not depend on trust. We start with the usual digital currency framework (framework of coins made from digital signatures), which provides strong control of ownership, but this solution is incomplete without a way to prevent double spending. 为了解决这个问题,我们提出了一个点对点网络,它使用 proof-of-work 记录交易的公共历史,如果诚实节点控制了大部分 CPU 算力,攻击者要改变交易历史,在计算上,就很快变得不切实际。 To solve this problem, we proposed a network of point-to-points, which uses proof-of-work to record the public history of the transaction, and if honest nodes control most CPU computing, the attacker will quickly become impractical in terms of calculation if he wants to change the history of the transaction. 该网络强健之处,在于其非结构化简单性( unstructured simplicity ) 。节点们几乎不协调,全部立即工作( work all at once with little coordination )。节点们不需要被识别,因为消息不会被路由到任何特定地方,消息只需被尽力发送 ( delivered )。节点可随意离开,随意重新加入网络,接受 proof-of-work 链作为他们离开时所发生事件的证明。他们用他们的 CPU 算力进行投票,通过致力于扩展有效区块,表达他们对有效区块的接受;通过拒绝致力于无效区块,拒绝无效区块。任何所需规则和激励措施,都可通过这种共识机制强制执行。 The strength of the network lies in its unstructured simplicity. Nodees work almost unharmonized, all immediately (work at once with little coordination). Nodees do not need to be identified, because messages are not routed to any particular place, and messages are sent as much as they can (divered). Nodees can leave, re-enter the network at will, accept proof-of-work chains as proof of what happened when they left. They use their CPU calculations to vote and express their acceptance of effective blocks by working to expand them; and, by refusing to commit to invalid blocks, reject invalid blocks. Any rules and incentives required can be enforced through this mechanism of consensus. [1] W. Dai, "b-money," http://www.weidai.com/bmoney.txt, 1998.(中译) [1] W. Daí, "b-money" 原文:https://bitcoin.org/bitcoin.pdf Original language: : Satoshi Nakamoto
[2] H. Massias, X.S. Avila, and J.-J. Quisquater, "Design of a secure timestamping service with minimal trust requirements," In 20th Symposium on Information Theory in the Benelux, May 1999.
[3] S. Haber, W.S. Stornetta, "How to time-stamp a digital document," In Journal of Cryptology, vol 3, no 2, pages 99-111, 1991.
[4] D. Bayer, S. Haber, W.S. Stornetta, "Improving the efficiency and reliability of digital time-stamping," In Sequences II: Methods in Communication, Security and Computer Science, pages 329-334, 1993.
[5] S. Haber, W.S. Stornetta, "Secure names for bit-strings," In Proceedings of the 4th ACM Conference on Computer and Communications Security, pages 28-35, April 1997.
[6] A. Back, "Hashcash - a denial of service counter-measure," http://www.hashcash.org/papers/hashcash.pdf, 2002.
[7] R.C. Merkle, "Protocols for public key cryptosystems," In Proc. 1980 Symposium on Security and Privacy, IEEE Computer Society, pages 122-133, April 1980.
[8] W. Feller, "An introduction to probability theory and its applications," 1957.
作者:Satoshi Nakamoto
译者 & 校对 :椰子加农炮,古拉 & 椰子加农炮? @ 币未来 biweilai.com
interpreter & proofread: coconut cannon, gura & coconut cannon? @biweilai.com
注册有任何问题请添加 微信:MVIP619 拉你进入群

打开微信扫一扫
添加客服
进入交流群